The R3DTEAM.AI Methodology
Turning attacker-perspective monitoring into clear, prioritized actions to protect your business. We continuously discover your assets, probe them like an adversary, map to security frameworks, and tell you exactly what to fix first.
SIX PHASES OF THE ASSESSMENT
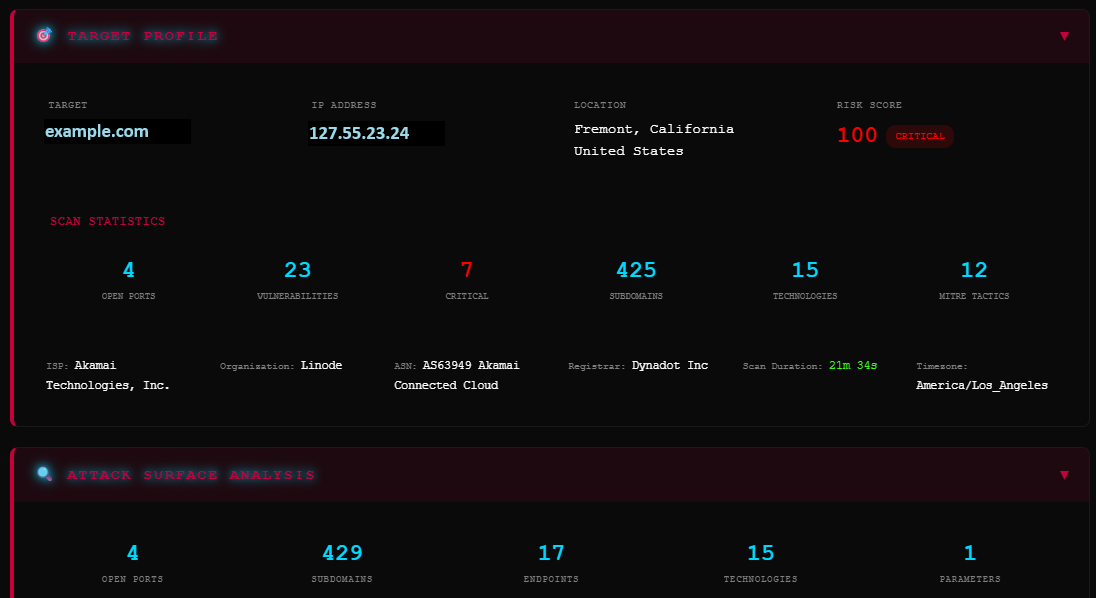
Asset Discovery
Know Your Attack SurfaceBefore you can defend your organization, you need complete visibility into what you're defending. Our automated discovery engine maps your entire external attack surface.
- ▹Domain enumeration and subdomain discovery
- ▹Reverse DNS lookups and WHOIS intelligence
- ▹Shadow asset detection
- ▹Certificate transparency log analysis
- ▹Cloud infrastructure fingerprinting
Reconnaissance
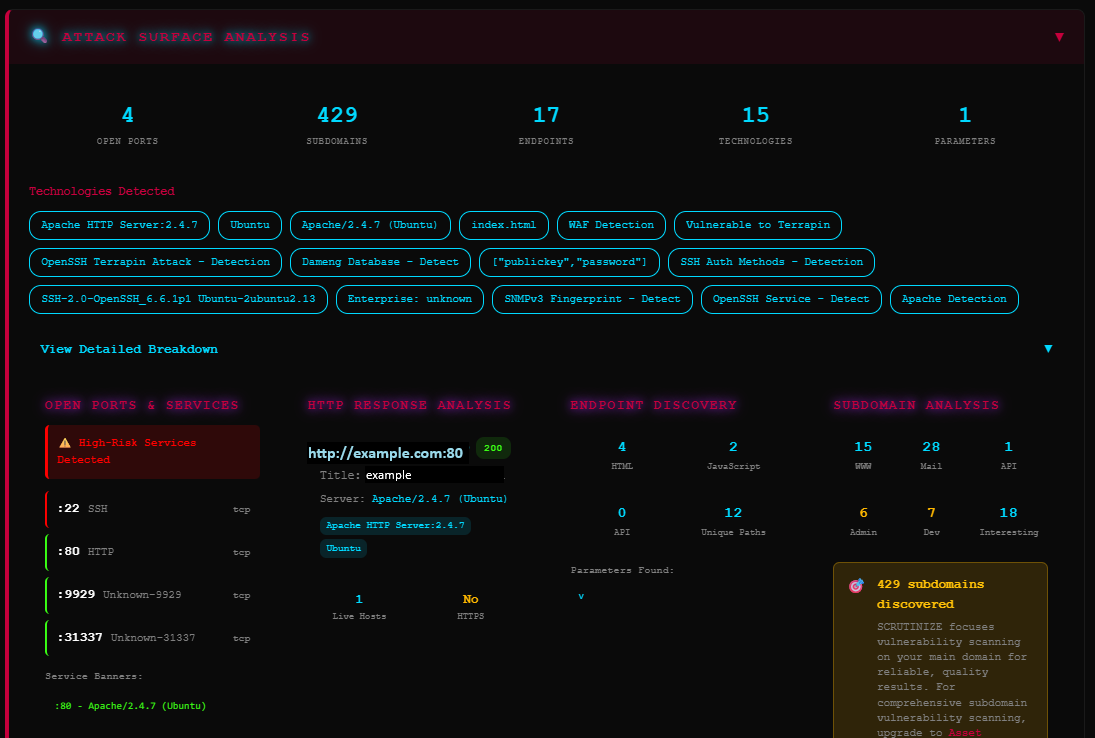
See What Attackers SeeWe perform the same reconnaissance that sophisticated threat actors conduct against your organization - but we do it first.
- ▹Full TCP/UDP port scanning
- ▹Service version identification
- ▹Technology stack detection
- ▹SSL/TLS configuration analysis
- ▹Web application fingerprinting
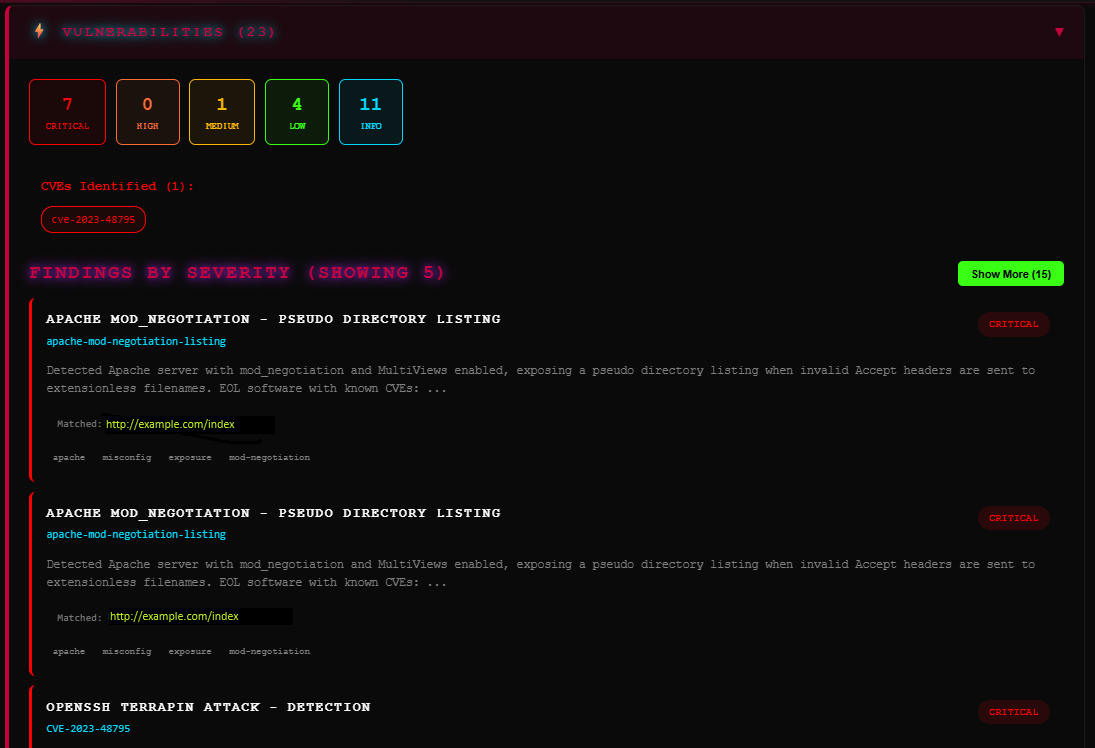
Vulnerability Assessment
Find Weaknesses Before Adversaries DoOur multi-engine vulnerability management platform correlates findings across industry-leading scanners and proprietary detection rules to validate exposures.
- ▹CVE detection with Nuclei templates
- ▹CISA Known Exploited Vulnerabilities (KEV) correlation
- ▹EPSS scoring for exploitation probability
- ▹Configuration weakness identification
- ▹Default credential detection
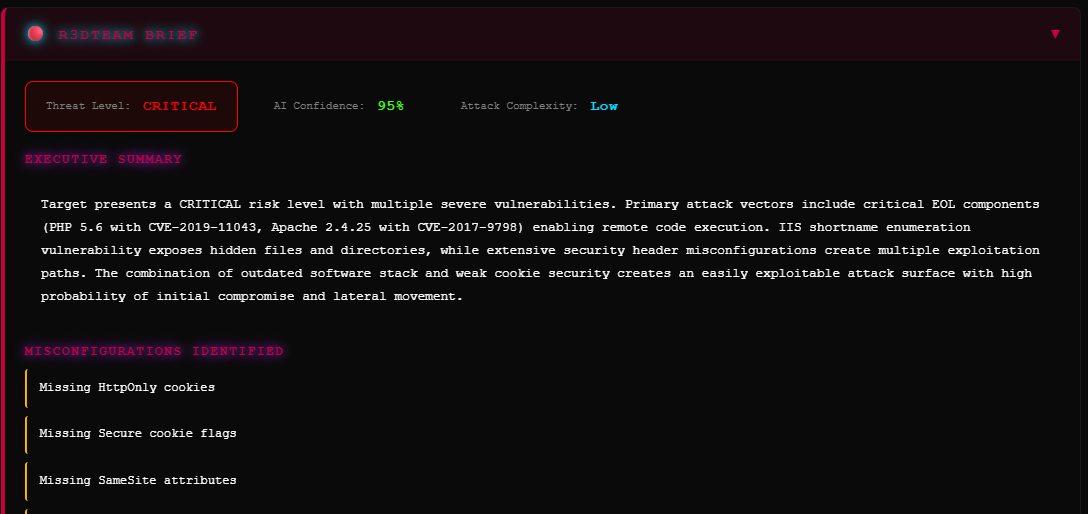
Analysis & Intelligence
Think Like the AdversaryRaw vulnerability data isn't actionable. Our analysis engine contextualizes findings through the lens of real-world attack patterns and threat intelligence.
- ▹Attack chain analysis
- ▹Threat actor TTP correlation
- ▹Business impact assessment
- ▹Penetration testing roadmap generation
- ▹Executive briefing summaries
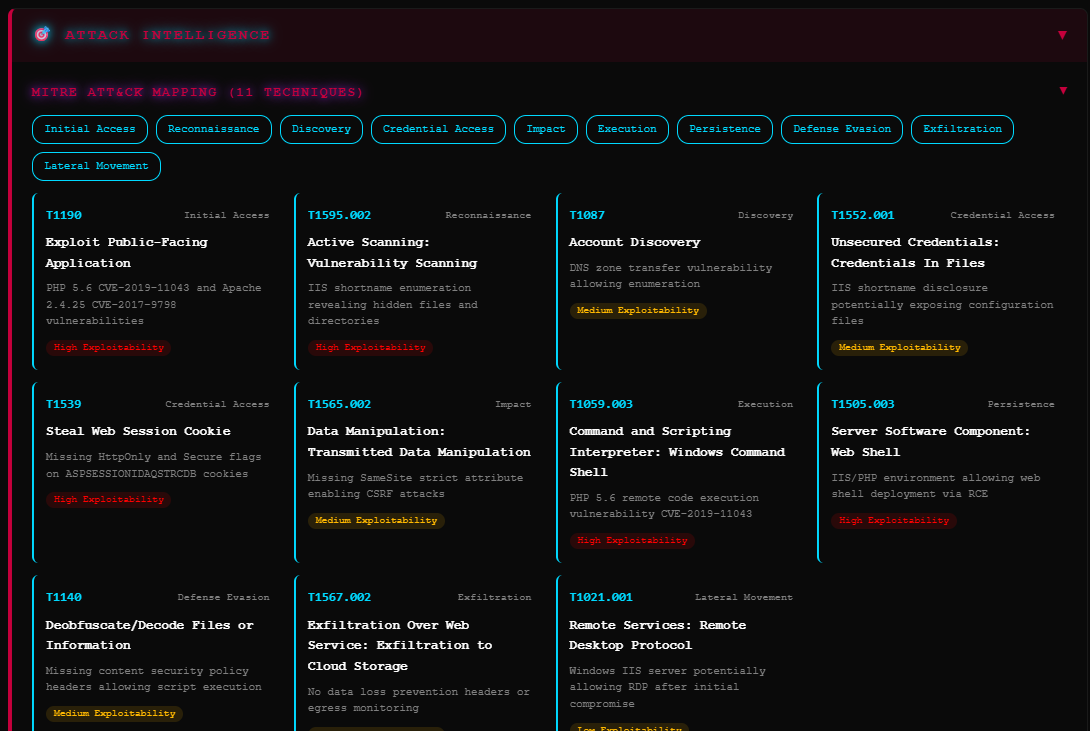
Framework Mapping
Align to Industry StandardsEvery finding is mapped to industry-standard frameworks, enabling clear communication with stakeholders and alignment with compliance requirements.
- ▹MITRE ATT&CK technique mapping
- ▹MITRE D3FEND defensive recommendations
- ▹CIS Controls alignment
- ▹NIST Cybersecurity Framework mapping
- ▹Kill chain stage identification
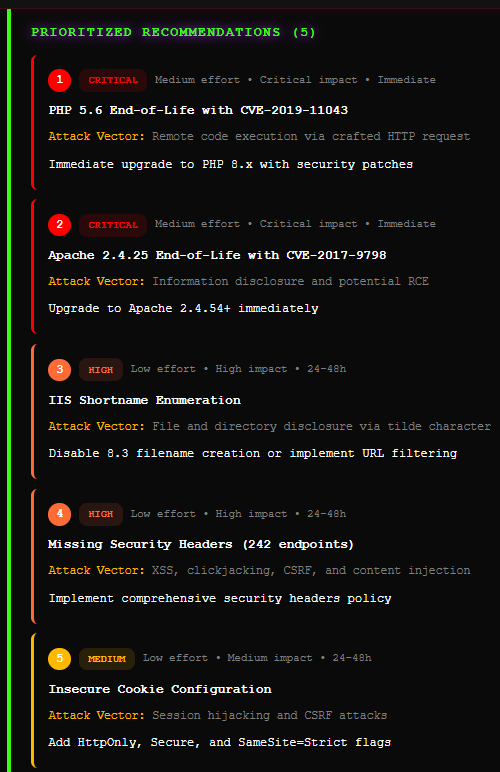
Actionable Recommendations
Remediate with ConfidenceEvery finding includes specific, actionable remediation guidance aligned with industry frameworks and your technology stack.
- ▹Step-by-step remediation instructions
- ▹Priority-based remediation roadmap
- ▹Risk-ranked findings
- ▹Technology-specific guidance
- ▹Verification steps
Why R3DTEAM
Continuous Monitoring
Not just point-in-time scans. Continuous baseline tracking with daily delta analysis catches new exposures as they emerge.
Attacker Perspective
Every assessment is conducted from the adversary's viewpoint - external, unauthenticated, exactly how a real attacker would approach your organization.
Practitioner Expertise
Built by red team operators with decades of combined experience in penetration testing, incident response, and threat intelligence.
Speed at Scale
Complete attack surface assessments in minutes, not weeks. Scale from single domains to enterprise portfolios.
Ready to See Your Attack Surface?
Start monitoring and discover what adversaries can see about your organization.